This Is the Era of the High-Value Cyber Problem Solver
The cybersecurity “talent shortage” has been overstated. There aren’t millions of jobs sitting empty for eager graduates - and even seasoned professionals can spend months searching for their next role.
Yet, despite this reality, opportunity has never been greater.
In this post, I’ll show you how to rethink the cybersecurity job market, understand what’s actually happening beneath the headlines, and position yourself to take advantage of the real opportunities that exist right now.
Reality Check: Growth Happened, Not the Hype
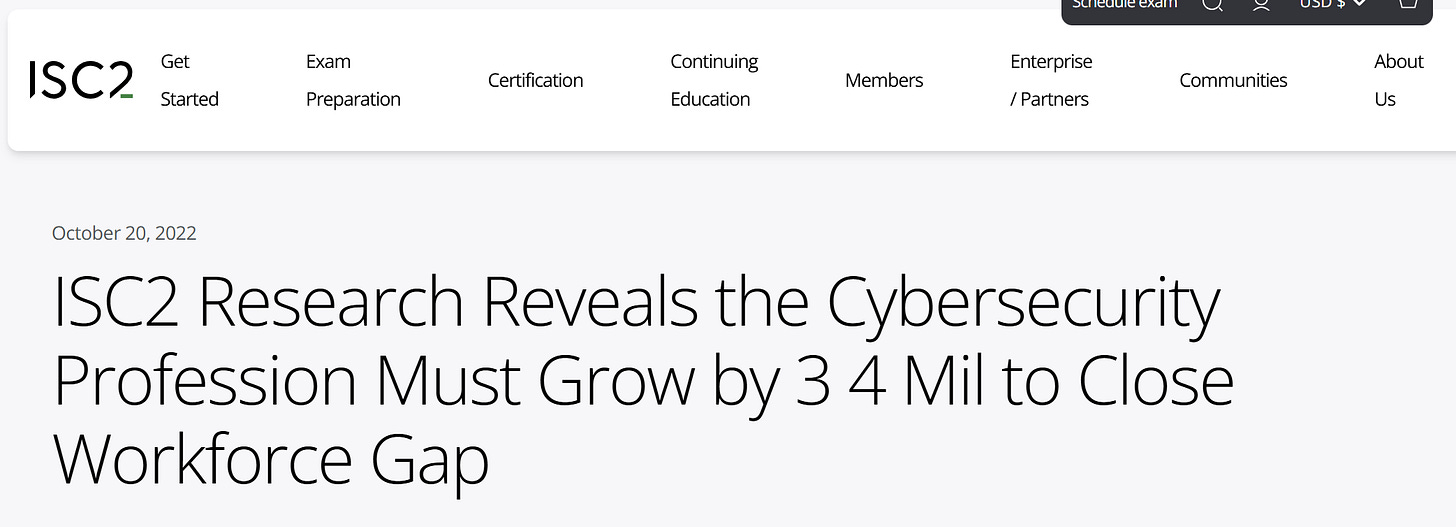
The image below shows a 2022 study by ISC2 reporting that the cybersecurity profession needed to grow by 3.4 million individuals worldwide to close the workforce gap.
This is one of many studies that estimate workforce demand based on survey responses, such as: “72% of respondents expect their cybersecurity staff to increase somewhat or significantly within the next 12 months.”
The reality is that cybersecurity has grown. Industry associations are larger than ever, and major enterprises that once had security teams under 100 people now operate with several hundred.
The misconception for graduates came from two places.
First, many believed employers would hire and train university graduates for roles that actually require hands-on skills and a deep understanding of technology.
Second, the projected explosion in open roles never reached the scale those studies predicted.
This doesn’t mean you can’t break into cybersecurity today. It means you need a different mindset - one that understands how the market really works and how to create an edge.
The Real Problem: You Were Never Properly Trained
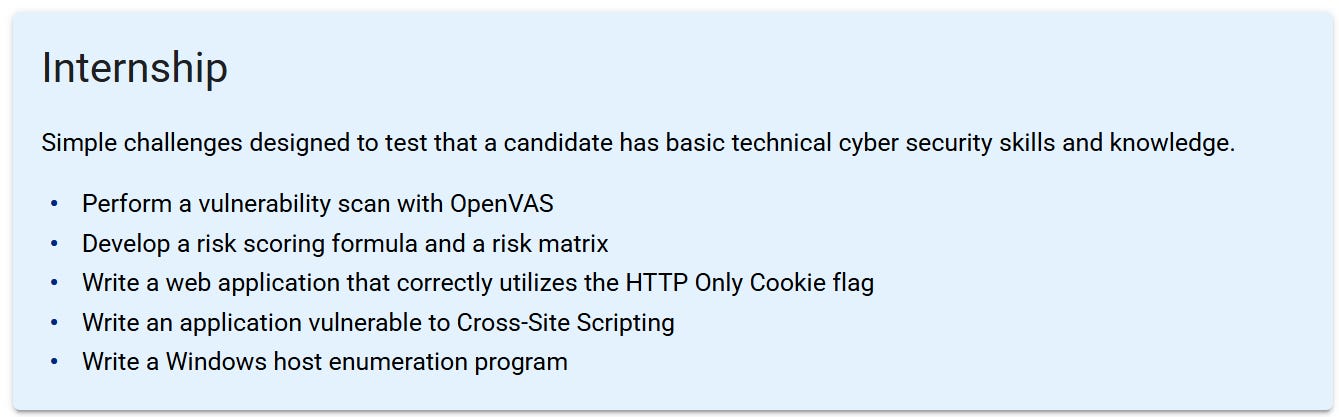
At Mossé Security, we offer an internship position that requires zero prior cybersecurity experience. Our goal is to identify newcomers with talent, critical thinking ability, and strong problem-solving skills.
Each year, we receive between 600–800 applications. We don’t read CVs or review LinkedIn profiles. Instead, we send candidates a technical aptitude test to determine whether they meet a minimum baseline of practical skills:
Some years, we already have enough interns, so we simply ask candidates to re-apply in six months. Other years, we’ve sent the aptitude test to every single applicant. What we consistently discovered is that only 5–15 people per year can pass this baseline test.
Since the launch of ChatGPT, we noticed a shift - candidates who previously struggled began leveraging AI to complete the assessment. To adapt, we raised the bar slightly. We now evaluate whether a candidate can use tools like GPT effectively without becoming dependent on them. The goal isn’t to exclude AI-assisted applicants - it’s to identify those who understand the technology well enough to incorporate it intelligently, not hide behind it.
The biggest challenge for most graduates is simple: they don’t yet have skills that solve problems worth paying for. If you’re expecting employers to train you from scratch, you’re putting yourself at a disadvantage.
Companies aren’t hiring to run training programs - they’re investing in automation to scale existing teams, outsourcing where quality allows, and prioritizing efficiency. Most employers don’t see themselves as training organisations. They expect contributors, not apprentices.
The Market Rewards Problem-Solvers — Massively
The cybersecurity market has experienced explosive growth and forecasts show strong continued expansion:
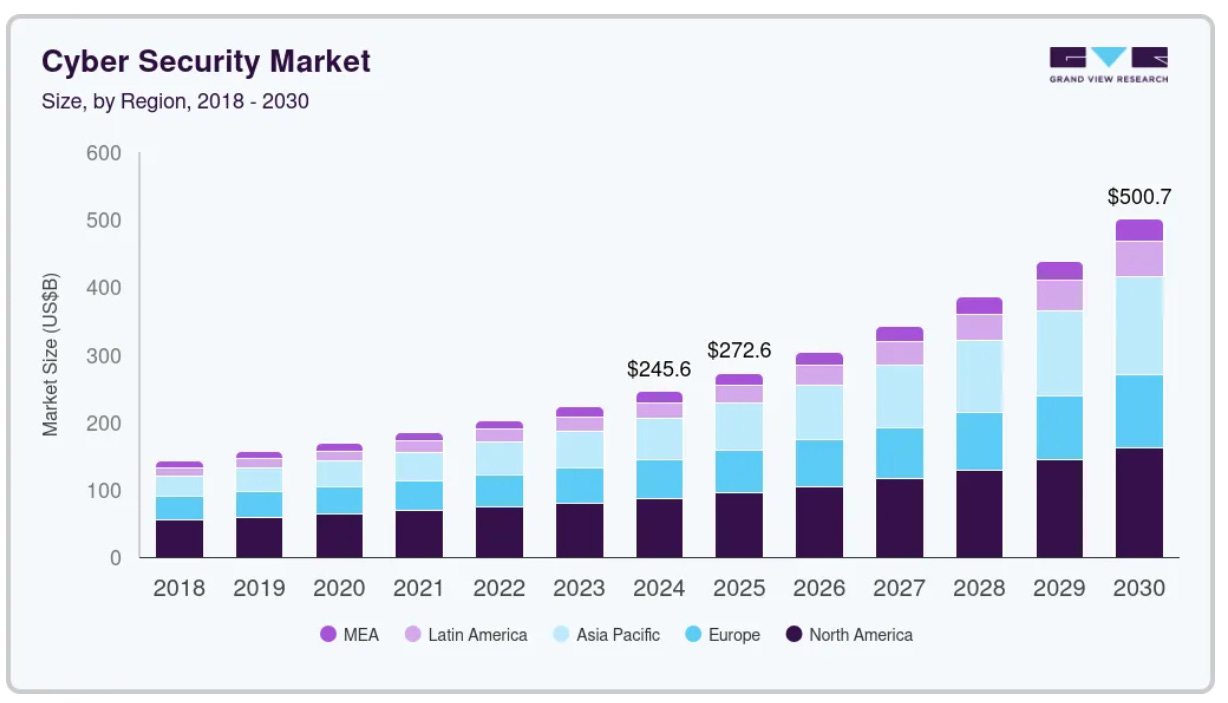
The opportunity isn’t just large — it’s enormous. There is more than enough demand and capital in this industry for capable problem-solvers to achieve their financial goals.
Look at the largest companies in your region, and the fastest-growing ones. Every single one of them needs competent cybersecurity talent.
To win opportunities you need three things:
A champion inside the organisation
A clear point of view on how you will solve high-value problems for their business
Proof that you can deliver, not rhetoric
The hardest part of this formula is finding a champion. Everything else is within your control right now — no permission needed, and with skills you can build to become unstoppable.
Nothing stops you from learning application security and threat-modelling the software built by the companies you want to work for.
Nothing stops you from researching vulnerabilities in a specific technology and reaching out to CTOs, CIOs, and CISOs whose organisations depend on it.
The key is in how you communicate. You don’t push. You don’t demand a meeting. You don’t ask for money.
You write in a way that shows you’re here to help, to build trust, and to take initiative on meaningful security problems — if they decide it matters. And they will.